
艾因交流程序

- 文件大小:18.2MB
- 界面语言:简体中文
- 文件类型:Android
- 授权方式:5G系统之家
- 软件类型:装机软件
- 发布时间:2025-08-18
- 运行环境:5G系统之家
- 下载次数:451
- 软件等级:
- 安全检测: 360安全卫士 360杀毒 电脑管家
系统简介
你有没有想过,那些我们每天离不开的软件,它们是如何确保我们的信息安全呢?今天,就让我带你一起揭开软件安全验证流程的神秘面纱,用一张图解的方式,让你一目了然!
一、初识软件安全验证
首先,得先了解一下什么是软件安全验证。简单来说,就是通过各种手段和方法,确保软件在开发、测试、部署和运行过程中,能够抵御各种安全威胁,保护用户数据不被泄露或篡改。
二、软件安全验证流程图解
接下来,我们就用一张图来展示整个软件安全验证的流程。
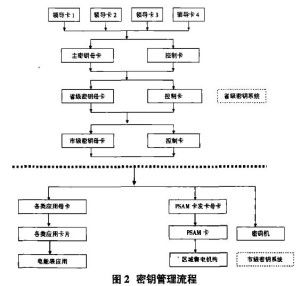
------------------ ------------------ ------------------
| | | | | |
| 需求分析 ----> 设计阶段 ----> 开发阶段 |
| | | | | |
-------- --------- -------- --------- -------- ---------
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| |
常见问题
- 2025-12-19 hmscore非华为手机安装
- 2025-12-19 小说排行榜
- 2025-12-19 火绒安全软件app下载
- 2025-12-18 远方软件库
装机软件下载排行

其他人正在下载
- 芒物元宇宙商城
- 时尚芭莎手机版
- nice数藏app
- 日淘酱代购安卓版
- 美多萌最新版
- 生动科学免费版
- tokenpocket最新v1.8.7版下载
- 小狐狸官网钱包最新版
- Letstalk官方正版
- whatsapp官方最新版下载






